Event Triggers
An Event trigger raises the alert when a certain event fires in a context, and conforms to a condition specified in trigger settings. This event may be generated by Iotellect Server itself or may come from a Data Terminal.
The event trigger's properties are described here. Each trigger causes Iotellect Server to "listen" for the event specified by the Event setting in every context that matches the Context Mask setting. When such an event is detected, the server evaluates the expression specified by the Expression setting. This expression usually refers to some data associated with the event, but it may also refer to any other data, such as the values of some context variables.
 | If the Expression parameter is not specified, every occurrence of the event will raise the alert. |
 | Example of event trigger: Let's say we're running a vehicle monitoring system, which has Devices in various factory vehicles. These Devices fire various events, such as the Impact event, which fires when the vehicle bumps (or crashes...) against something. So the Context Mask would match the Device monitoring the vehicle, the event would be something like impact, and we could also have an expression, referring to the strength field of the impact event, which would cause the trigger to activate if the strength of the impact exceeds a certain value. In this case, the Event Trigger parameters may be as follows: |
 | Example of event trigger expression: This expression will trigger an alert if a message is received from Syslog server:
|
Multiple Events Trigger
Count and Period trigger parameters work together to allow trigger activation only if event occurred X times within last Y seconds.
If Count is set to 1 (default), any event matching trigger Expression will activate the trigger and alert. If Count is 3 and Period is 10 minutes, the trigger will be activated upon an occurrence of event if two previous occurrences happened not more than 10 minutes ago and all three occurrences match an Expression.
 | Example: let's assume we're monitoring several servers in a network. A single "Authentication Failed" event received from any server does not necessarily indicate a problem, since user may have just mistyped his password. However, multiple events received from a single server within 10 minutes should raise a security alert. Here is a proper event trigger setup for this case: |
Event Correlation
 | Event correlation is a technique for making sense of a large number of events and pinpointing the few events that are really important in that mass of information. |
In terms of Iotellect alerts, event correlation is a way to activate the alert by an event trigger when one ("primary") event occurs, and deactivate the alert upon another ("correlated") event.
To enable event correlation for a certain event trigger, specify the name of the Deactivation Event in the trigger settings. In this case:
Event trigger (and the alert itself) will be activated by the event named in the Event setting (which is the "primary" event in this case).
It will be deactivated if Deactivation Event occurs in the same context with Event, and additionally, Deactivation Expression evaluates to TRUE. (It can happen that the Deactivation Event occurs, but Deactivation Expression evaluates to FALSE, thus leaving the trigger active.)
 | Once a trigger has been activated, it switches the alert to Active state and adds an Active Instance. |
The following picture illustrates activation/deactivation of event trigger by Primary and Correlated events:
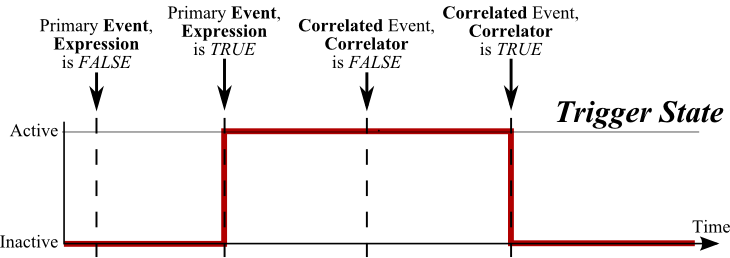
 | Count and Period settings also work for correlated events. For example, if Count equals to 5 and Period is 1 minute, trigger will be deactivated only if five events defined in the Deactivation Event occur within one minute and all five will match Deactivation Expression. |
 | Examples of event triggers using event correlation: Sometimes we may want to view an alert in the Active Alerts list when a certain device is offline (not available for Iotellect Server). Assuming that we have connection and disconnection events in the Device context of this device, we may use the following event trigger settings to force an alert remain active when device is disconnected: |
Trigger Message
In addition to alert's Message expression, each event trigger has its own Trigger Message expression. This expression is resolved to a string when the alert is raised. The resulting string becomes a part of Alert Event, holding any custom information about alert cause or other circumstances.
 | Example of event trigger message expression: This expression can be used to insert value of a certain custom SNMP trap 's variable binding into an alert. The expression first refers to a nested table of SNMP Trap's event data table using |
Resolution Environment
Event Trigger Expression and Deactivation Expression Resolution Environment: | |||
Context the event was received from. | |||
Data Table containing event-specific data for trigger event or correlated event. | |||
0 | |||
Variable Name | Value Type | Description | |
|---|---|---|---|
context | String | Full path to the event's context. | |
event | String | Name of the event. | |
level | Integer | Event level. | |
time | Date | Event timestamp. | |
acknowledgements | Data Table | Event acknowledgements table. | |
enrichments | Data Table | Event enrichments table. | |
Was this page helpful?