Mass-Enabling Remote Access to WMI
When deploying Iotellect in large networks, it's often necessary to enable WMI on hundreds or even thousands of workstations. This article is a step-by-step instruction for that.
There are two top-level operations to be completed:
1. Setting up Group Policies
The group policies are created and configured on a Domain Controller machine.
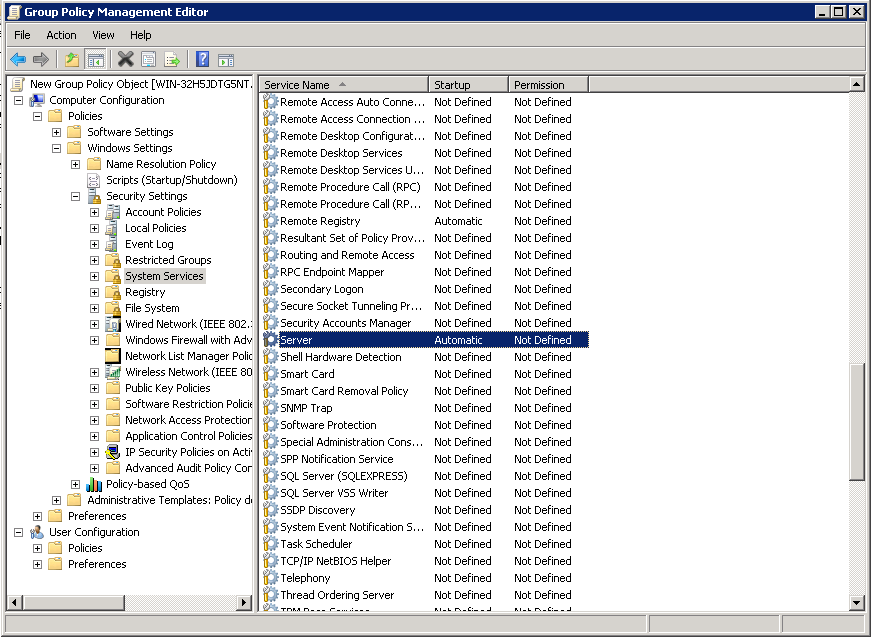
2.1 Enable Server and Remote Registry Services
Use group policies to enable Server and Remote Registry Services.
2.2 Enable DCOM Access
Use group policies to enable DCOM access.
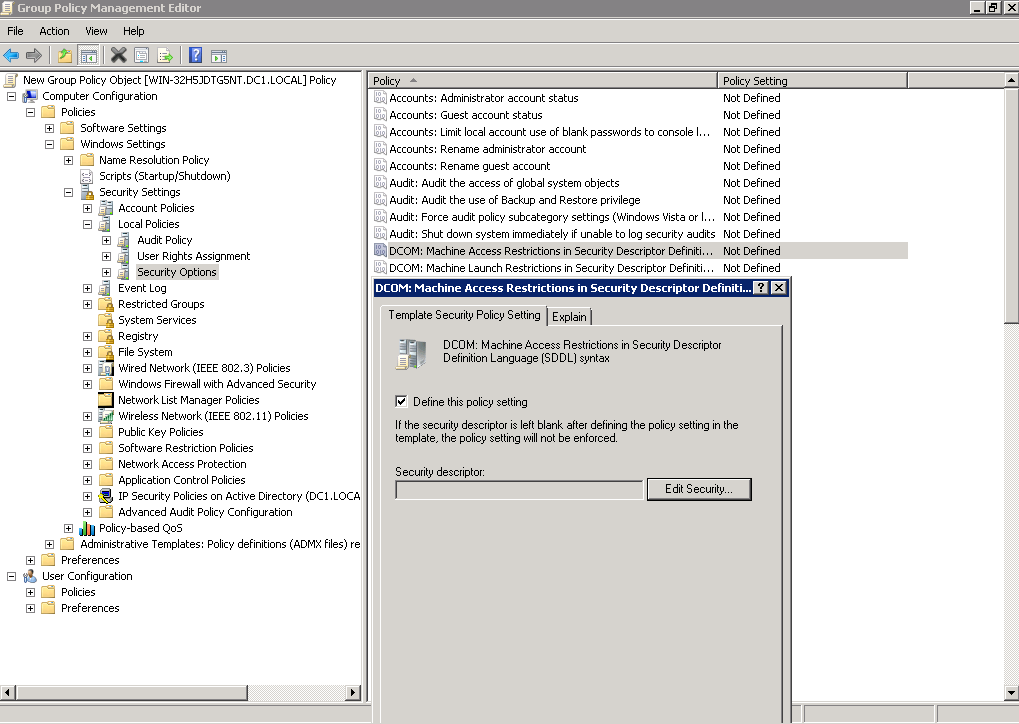
2.2.1. Double click on a DCOM: Machine Access Restrictions policy, then use Edit Security button to add a user whose credentials will be used for monitoring.
Give this user Remote Access permissions.
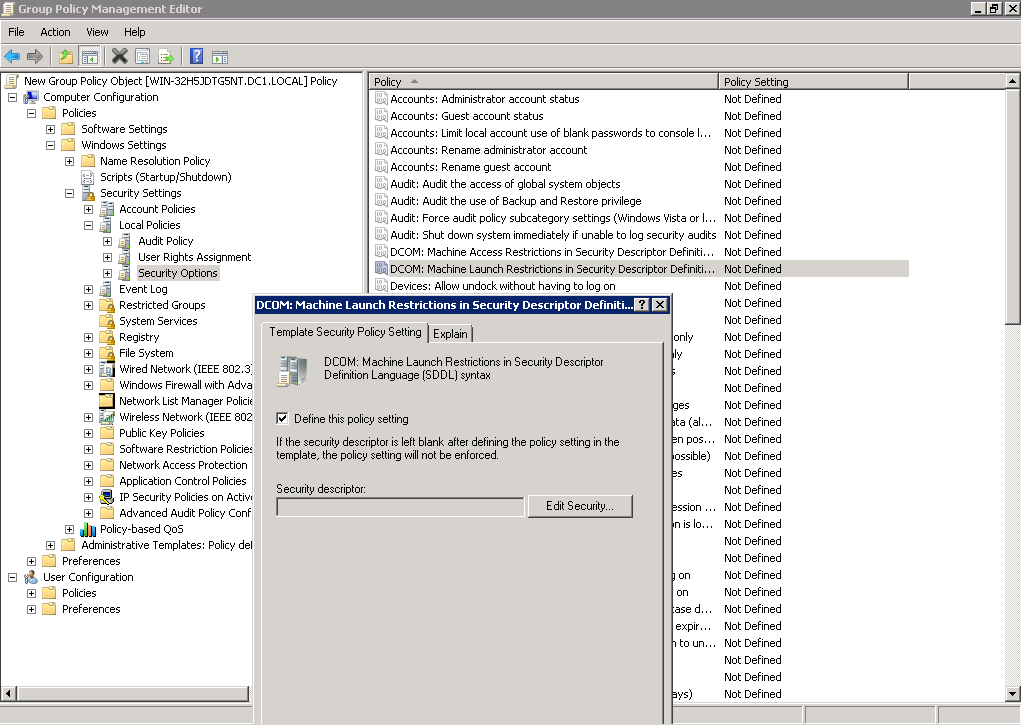
2.2.2. Double click on a DCOM: Machine Launch Restrictions policy, then use Edit Security button to add a user those credentials will be used for monitoring.
Give this user Local Launch, Remote Launch, Local Activation, and Remote Activation permissions.
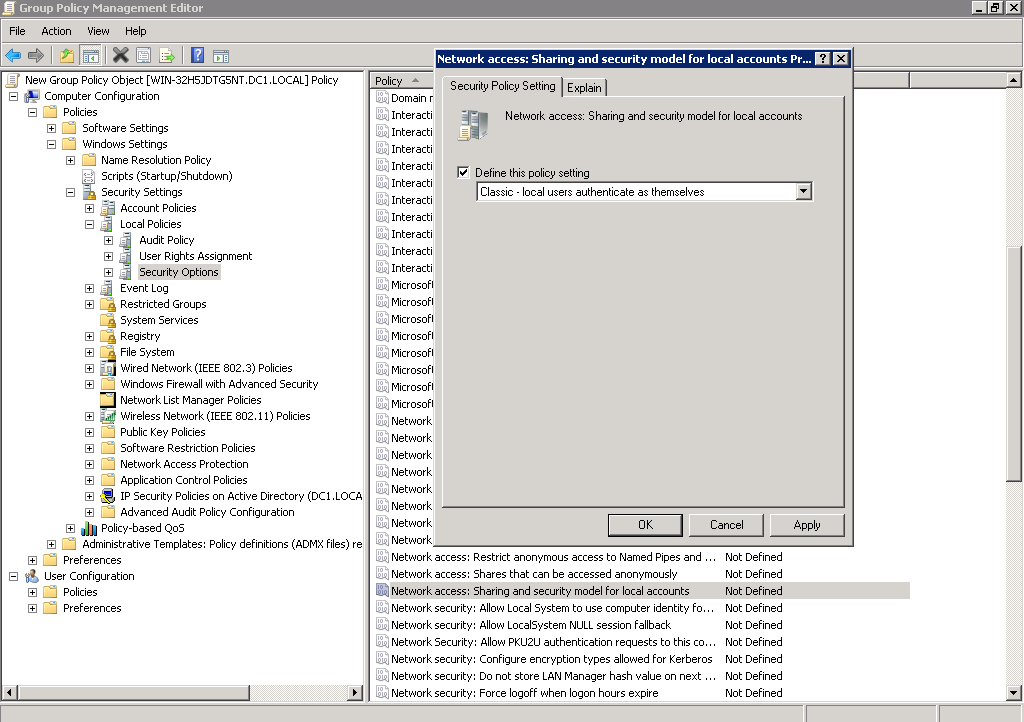
2.2.3. Double-click Network access: Sharing and security model for local accounts policy, select Classic - users authenticate as themselves from a drop-down list.
2.3 Configure or Disable Windows Firewall
Reconfigure Windows Firewall using group policies if necessary.
In some cases, Windows Firewall is configured to block the DCOM protocol. Make sure that Windows Firewall does not block DCOM protocol or is disabled.
2.4 Disable User Account Control (UAC)
When User Account Control (UAC) is active, an administrator account actually has two security tokens, a normal user token, and an administrator token (which is only activated when you pass the UAC prompt). Unfortunately, remote requests that come in over the network get the normal user token for the administrator, and since there is no way to handle a UAC prompt remotely, the token can't be elevated to the true-administrator security token.
Thus, UAC should be disabled via group policies to allow remote DCOM access.
2.4.1. Set User Account Control: Behaviour of the elevation prompt for administrators in Admin Approval Mode policy to Elevate without prompting
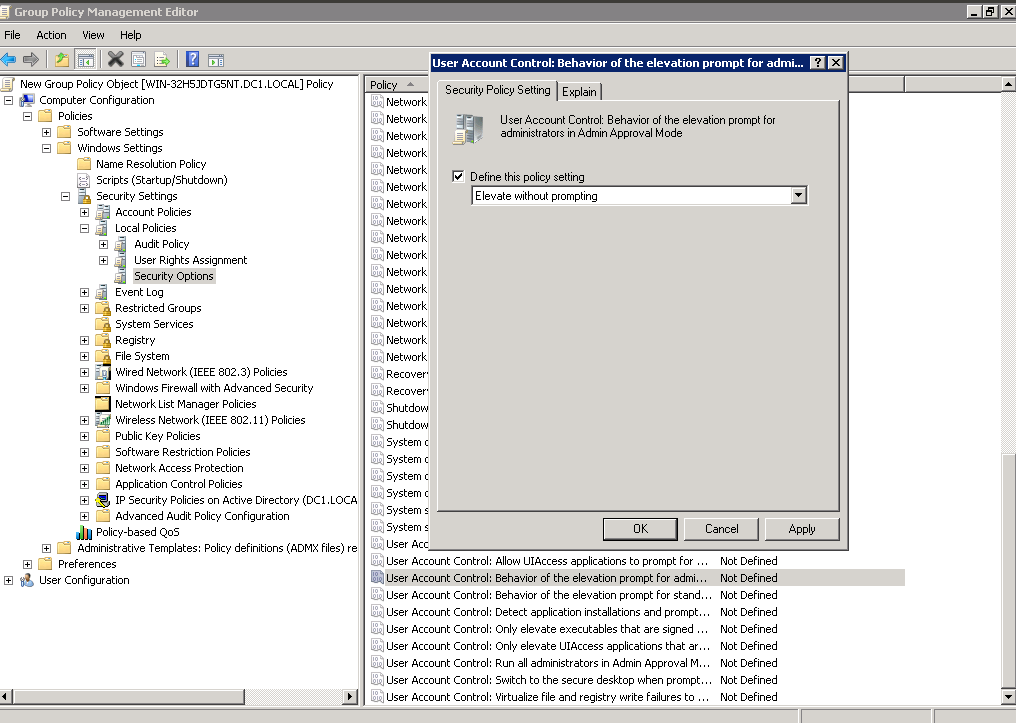
2.4.2. Set User Account Control: Detect application installations and prompt for elevation policy to Disabled
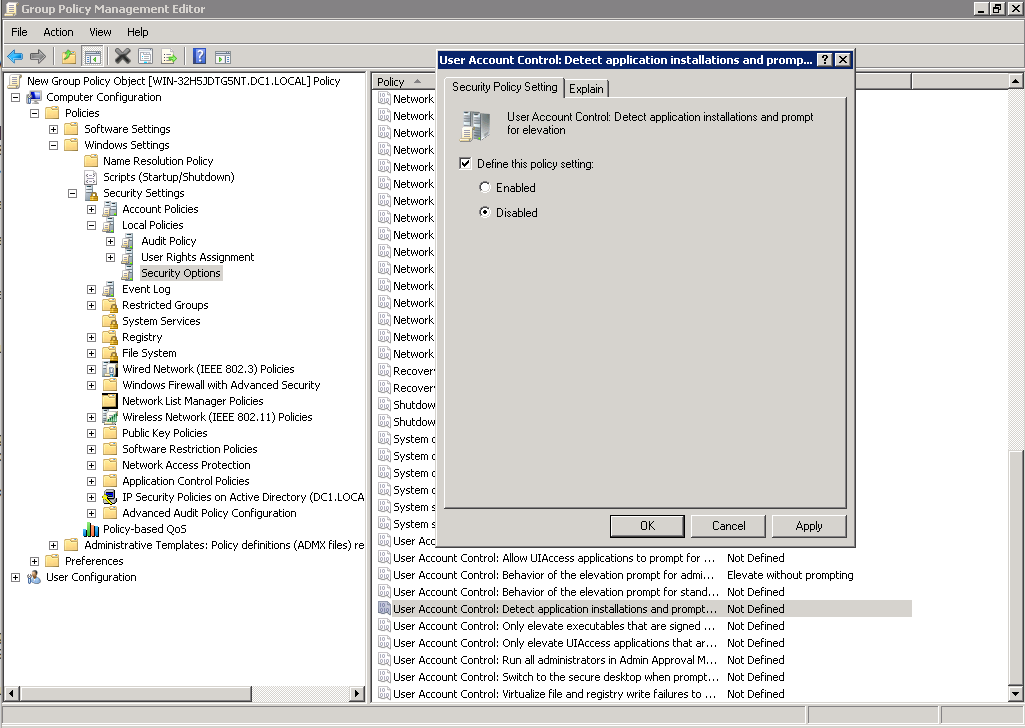
2.4.3. Set User Account Control: Run all administrators in Admin Approval Mode policy to Disabled
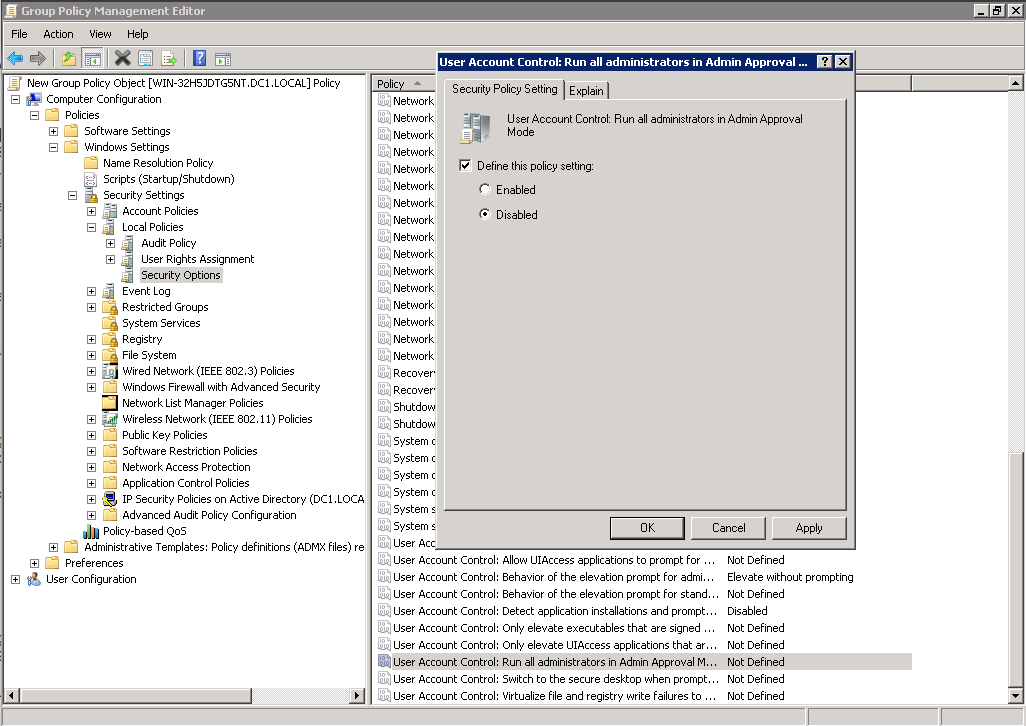
2.5 Enable WMI Access Through Windows Firewall
Reconfigure Windows Firewall using a group policy to pass WMI requests:
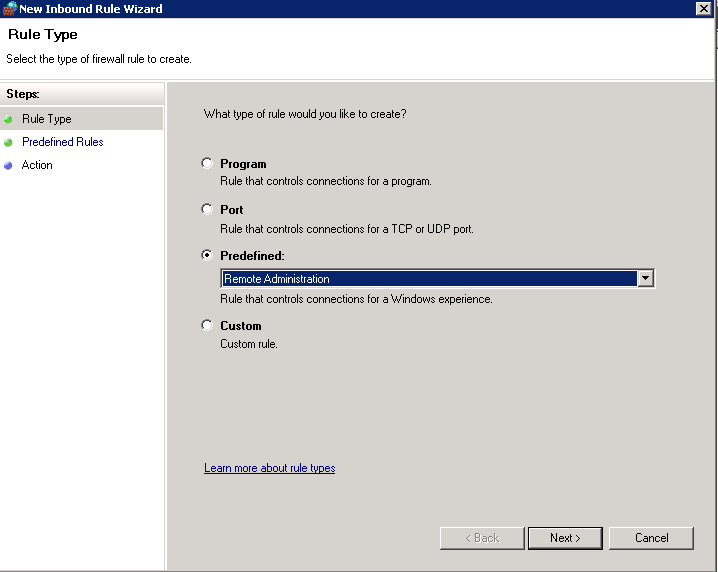
2.6 Configure WMI Impersonation
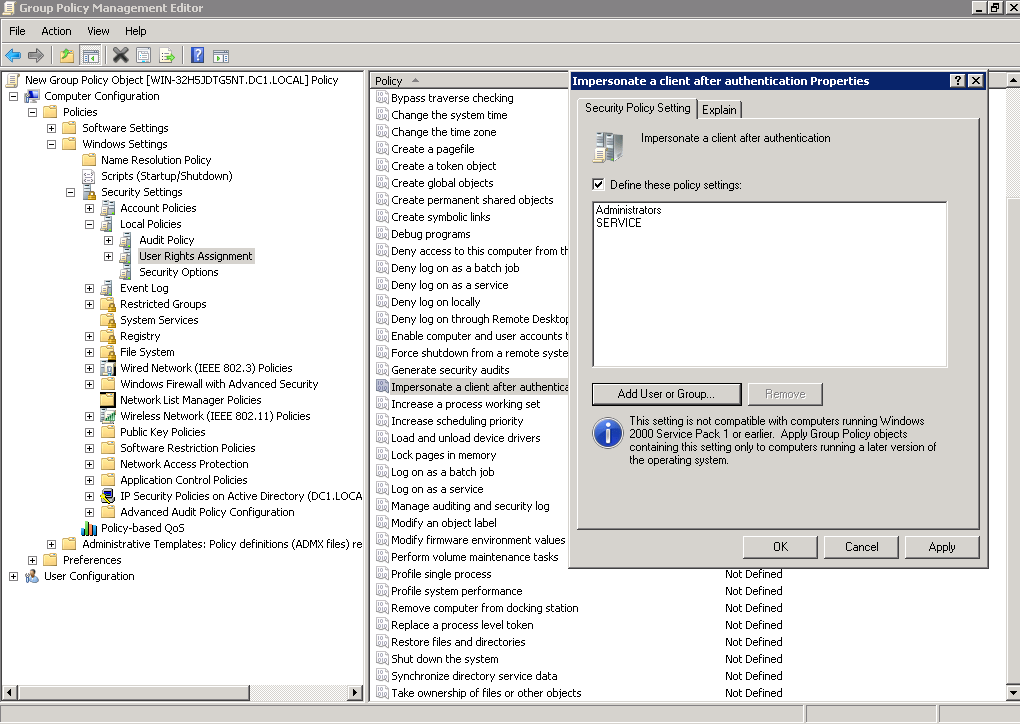
Go to Security Settings > Local Policies, then select User Rights Assignment. Make sure that Impersonate a client after authentication policy grants permissions to the SERVICE system account.
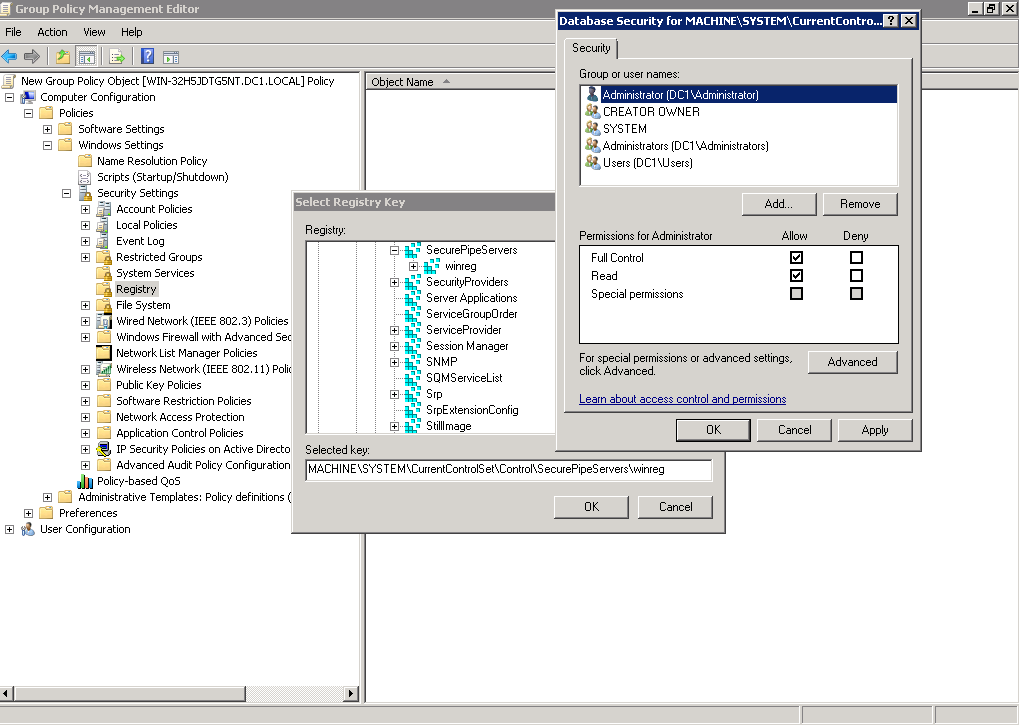
2.7 Configuring Registry Permissions
Grant the user those credentials will be used for monitoring Full Control permissions to HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurePipeServersWinReg registry branch.
2. Running WMI Configuration Script
The WMI configuration script does the rest of mass WMI configuration job. Once it's finished, you can connect WMI hosts to Iotellect for monitoring.
The script is written in PowerShell. Script text is available in a separate article.
Run instructions:
wmi_config.ps1 file.Set-ExecutionPolicy RemoteSigned command.Find Hosts Ready for WMI Configuration
To create a file listing all hosts in your network that are ready for WMI configuration (e.g. have RPC port (135) open), use another PowerShell script.
Automatic WMI Enabling
The WMI hosts scanning script and the WMI configuration script can be started periodically using Windows Task Scheduler. This will allow to auto-discover and auto-connect all new WMI hosts to Iotellect by using Iotellect's network discovery feature thereafter.
Was this page helpful?